September 14, 2020, came to be the day of doom for many Magento merchants. Over 2,800 Magento 1 stores were hacked to steal credit card details in the largest documented campaign to date.
It’s not unusual for hackers to wreak havoc across ecommerce websites. Computer malware, viruses, worms, trojans, and many other ecommerce frauds… there’s a lot of nasty stuff floating around the net. There will always be someone trying to take advantage of a vulnerable system or gaining unlawful access with malicious intent.
If you don’t want to become a part of the next Magento security breach, this guide is for you. Read on to discover the main Magento security vulnerabilities and ways to prevent them so that your data and your customers’ data are safe.
First Things First, What’s the Problem with Magento 1 Security?
The prime problem of Magento 1 is that it is no longer supported. As of June 20, 2020, Adobe announced the end-of-life for its Magento 1 product, thus, making the platform edition obsolete and vulnerable to cyberattacks.
There you have the reason for a MageCart attack mentioned earlier. Outdated Magento stores remain attractive targets for those determined to steal personal and financial data from online customers.
Hackers can easily scan for outdated versions of Magento and use automated bots to access them, upload shell scripts, and install the card skimming malware. Card skimming attacks are undetectable by end-users, so the responsibility falls on website operators to update their systems to the latest version of Magento. At this point, any website using Magento 1.x should be assumed compromised.
— Paul Bischoff, a privacy advocate with Comparitech.
That’s why Magento store protection should be the #1 priority for merchants. Magento 1 isn’t secure and will never be. But Magento 2 will keep you in safe hands.
Lessons Learned and Implemented in Magento 2 Security
If you’re bitten by a tick, removing yourself won’t stop the infection. The same happened with Magento. After the critical vulnerability was found in Magento, an upgrade was necessary. So Adobe revamped the whole system to eliminate Magento security issues and protect their merchants from similar attacks in the future.
Here are Magento security features Adobe has introduced after Magento 1 end-of-life.
Enhanced Password Management
Magento 1 uses a weaker system of password hashing (a one-way process of turning a string of characters into what is known as a hashed password). To address this Magento vulnerability, Magento 2 supports Argon2ID13, a stronger hashing algorithm than the previous gold standard — SHA-256.

Improved Prevention of XSS Attacks
Magento has implemented new rules to prevent cross-site scripting (XSS) attacks by making escaped data the default.
XSS attacks are a type of malicious script injection used in phishing attacks, logging keystrokes, and other unauthorized activities.
More Flexible File System Ownership and Permissions
Starting in version 2.0.6, Magento allows users to set file systems access permissions. The recommendations are that certain files and directories be write-only in a development environment and read-only in a production environment.
Improved Prevention of Clickjacking Exploits
Magento safeguards your store from clickjacking attacks by using an X-Frame-Options HTTP request header. For more information, see the X-Frame-Options header.
Auto-Generating Encryption Key
Magento uses an encryption key to protect passwords and sensitive data. Currently, Magento 2 uses the AES-256 algorithm, and you can choose to generate a random key at any time through the admin panel.
Use of Non-Default Magento Admin URL
Hackers use automated password guessing bots to retrieve shoppers’ personal data and merchants’ access to the back-office operations. To prevent this type of attack, Magento by default creates a random Admin URI when you install the product.
Consistent Magento 2 Security Patches and Updates
The biggest reason why Magento 2 security trumps Magento 1 is regular updates. Adobe’s final Magento 1 security patch was released on June 22, 2020. Meanwhile, Magento 2 merchant get their security patches every quarter in an official Adobe Security Bulletin.
How Magento How Magento Minimizes the Impact of Vulnerabilities
In addition to the new architecture and security framework of Magento 2, there are processes in place to minimize the impact of vulnerabilities.
They include:
- Bug Bounty Program — Developers are rewarded bounties of up to $10,000 for bugs found in Magento. This is a great way to get the community involved in Magento security.
- Magento Security Center — New security updates, patches, best practices, and much more can be found on this resource. Whether you need more information about a patch or need instructions to install patches/updates, this is the place to go.
- Security Alert Registry — The Magento team responds to vulnerabilities and provides patches and updates to protect stores against threats. Subscribe to the Security Alert Registry to receive emails whenever there is a new security release.
- Code quality standards — The Magento core development team uses the Magento Coding Standard and recommends that developers who create Magento extensions and customizations also use this standard.
- Extension quality program — All extensions submitted to the Magento Marketplace go through a multi-step review process: technical and marketing reviews. If either review is not passed, the extension will not be allowed to be published.
Magento Security Checklist: What Security Standards Should Be in Place to Make Sure my Site Is Safe?
There’s no such thing as an unhackable site. Even if you hire the best-of-the-best developers, engineers, and security experts, there’s still a possibility of being hacked.
So, our recommendation is to enforce a strict security workflow for onboarding and day-to-day activities.
Here are ways of securing Magento:
- Include security practices in your onboarding process
Although this may seem self-explanatory, it’s often overlooked by both internal and external teams. Make sure new store employees, outstaffed employees, and everyone in-between goes through security onboarding. We recommend the CISO’s New Hire Onboarding Checklist. - Enforce strict access rights
Part of the onboarding process is figuring out what access rights an employee will need to do their job. Enforcing access rights to information is important and we also recommend doing access right reviews to make sure no rules are being violated behind your back. You can set up User Roles in Magento with this guide. - Make sure you comply with industry standards
This is both technical and business-wise. Your site and all the code used in it should comply with PHP coding standards, testing standards, and be PCI-compliant at all times. We’ll show you an actionable checklist in the next section so you can become PCI-compliant. - Have failover redundant infrastructure
Yes, we understand you’re not a security expert, but you need to ask whoever is responsible for security if they have a Backup Plan (which should cover what you backup, how often you backup, and when backups should be used). Important note: backups should be automated. - Secure third-party components (modules, services, extensions, applications)
Like the Magento Security Best Practices say, make sure all applications running on your server are secure. Avoid running applications like WordPress on the same server as Magento, because a vulnerability in one of those applications can potentially expose information from Magento. It goes without saying that you should never install extensions from untrusted sources (like torrent sites). - Protect your data
a. Infrastructure segregation
⇨ This is in line with securing third-party components. Under no circumstances should you have development, staging, and production environments running on the same server instance.
b. Limited access
⇨ Another point we touched upon: access rights extend to the developers and other IT personnel. Under no circumstances should every member of the team have full admin rights.
c. Personal data protection
⇨ Although it may seem obvious, part of the onboarding process should include not bringing in USB drives and other storage devices to work. Also, remember to not click on suspicious links or open suspicious emails. Never tell anyone your password (especially the Magento Admin password).
So with the boring stuff out of the way, let’s get down to bulletproofing your Magento store!
Bulletproof Magento Security: How to Secure Magento Site in 14 Steps

Step #1: Security Audit
There are a lot of moving parts in Magento security. No developer, architect, manager, or other roles understand There are a lot of moving parts in Magento security. No developer, solution architect, manager, or other roles understand security risks as well as a qualified security expert. That’s why the first step is to have your site combed through by an expert. Preferably, you should get this done at least once a year to stay secure.
Step #2: Automated Security Scan
Great news, you don’t have to go to a third party every time you want to run a scan. Magento offers its Security Scan free of charge.
Magento Security Scan allows you to monitor all of your websites (if you have more than one) for possible risks and highlights the patches and updates you require. Set a schedule (Magento recommends scanning on a weekly basis) and receive reports and corrective actions for each failed test. To get started, check out this guide.
There are also free scanning tools out there like MageReport, but it’s not as in-depth as Magento’s tool and does not offer automated or scheduled scanning.
Step #3: Magento Admin Security
Magento recommends a multilayered approach to securing your admin account(s).
You can:
- Set the security level for passwords
- Set the number of login attempts
- Configure length of keyboard inactivity before the session expires
- Require case-sensitive usernames and passwords
Admin passwords
On the Admin sidebar, go to Stores > Settings > Configuration.
In the left panel under Advanced, choose Admin.
Expand the Security section.
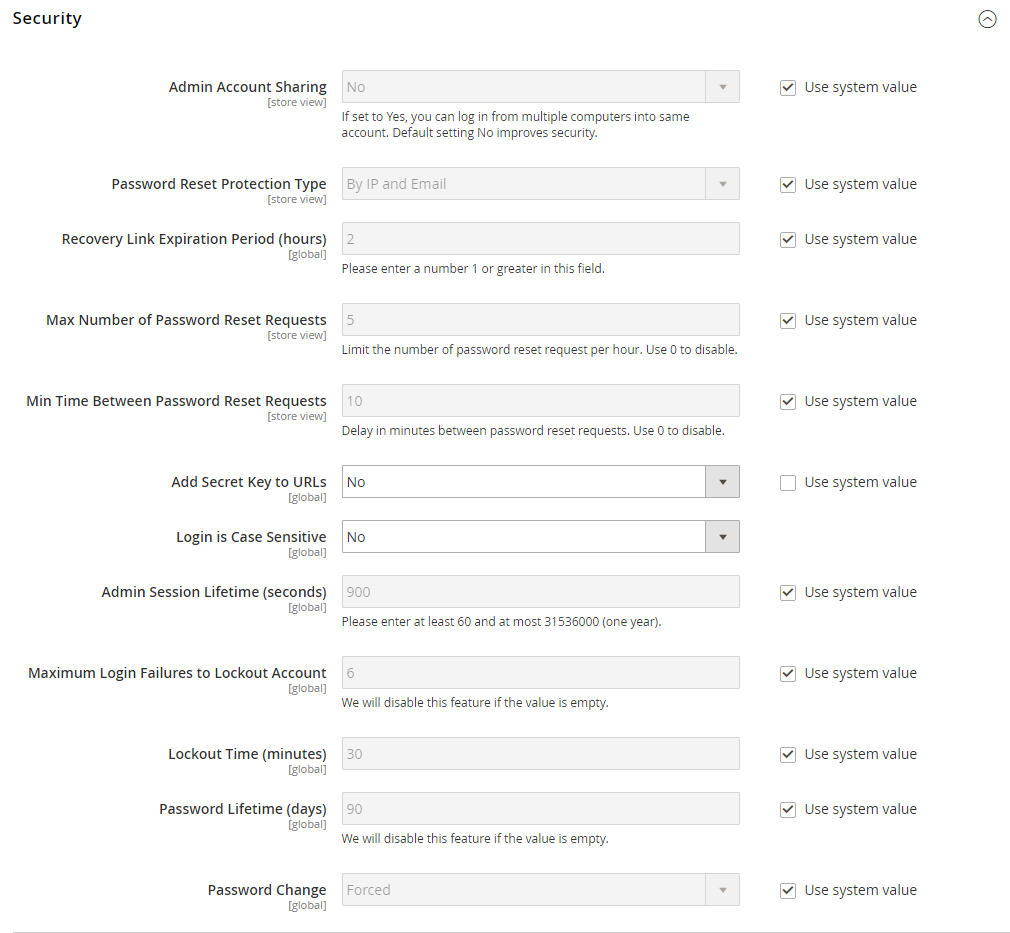
Change default Admin URL
It’s a good idea to change the default admin URL to something else to make it less of a target for hackers.
Default Base URL: http://yourdomain.com/magento/
Default Admin URL and Path: http://yourdomain.com/magento/admin
There’s a simple way to change the admin URL available in the admin panel, but keep in mind, any mistakes will render your site inaccessible to all admins, and the only way to fix it is by editing server configuration files (not something you want to experience, trust us).
IP Whitelisting
You might have heard of blacklisting — when you block access to a certain site, IP address, or network.
Whitelisting is the opposite — allowing access to certain information, sites, and in our case, the Magento admin panel, to only trusted IP addresses.
Step #4: Set User Roles
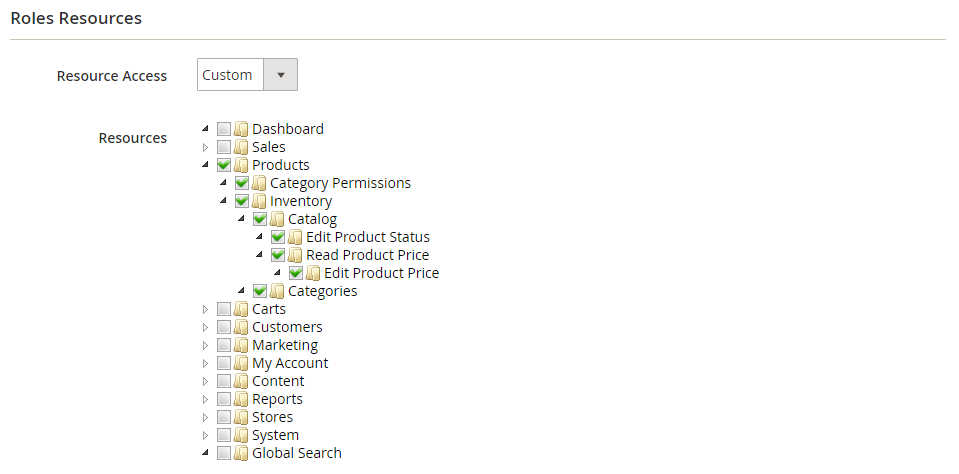
Magento includes options for restricting access for admins. In other words, you can create permissions to limit what a site admin sees and grant them limited access.
You can set up user roles by going to the Admin sidebar. Click System, under Permissions, choose User Roles. In the upper-right corner, click Add New Role.
After assigning a Role name and entering your password you can set up the Role Scope (see image below).
Magento Commerce allows you to log any actions performed by admins. You can turn on Action logs by navigating to Stores > Settings > Configuration. In the left panel, expand Advanced and choose Admin. Expand the Admin Actions Logging section and select the checkbox enable admin logging for each action you want to log.
Step #5: Configure Captcha and Google reCaptcha
In Magento, you can set up both Captcha and Google reCaptcha for admins and customers. Both protect you against spam and other types of automated abuse.
Captcha is a human validation test i.e. the blurry, squiggly letters and numbers you’ve probably had to squint to see.

Google reCaptcha is a superior type of human validation i.e. the “I Am Not A Robot” checkbox.
Invisible reCAPTCHA (Magento recommended) — which verifies a user is human automatically, without any interaction. It sounds like magic, but Google managed to find a way to do it.
Step #6: Two-Factor Authentication (2FA)
Two-Factor Authentication, or 2FA for short, is a method of confirming a user’s identity by making users complete a second step in the verification process. Magento 2FA is only available for Admin users and is not extended to customer accounts.
This is how you can configure 2FA in Magento:
On the Admin sidebar, go to Stores > Settings > Configuration.
In the left panel, expand Security and choose 2FA.
Step #7: Encryption Key
When you first fire up Magento, the system automatically generates an encryption key. This key is used to protect passwords and other sensitive data like credit card info and integration (payment and shipping module) passwords.
Magento recommends keeping this key safe and hidden at all times. If you experience a data breach, you can create a new encryption key to prevent anyone from accessing data using the old key.
You can generate a new key in the admin panel. To reiterate, we don’t recommend doing this on your own.
SStep #8: Password Requirements
Magento requires a minimum of seven characters (both letters and numbers). We recommend using something a bit more robust — a 10-12 character alphanumeric password.
Pro-tip — Don’t try to think of a password yourself. We recommend using LastPass to randomly generate a password.
Change your passwords if you suspect there’s a data breach, regardless of whether or not your account was hacked, and set a reminder to change your password once a year.
You can set the level of security for passwords used by both customers and admins directly in the admin interface
Password options for customers
On the Admin sidebar, go to Stores > Settings > Configuration.
In the panel on the left, expand Customers and choose Customer Configuration.
Expand the Password Options section.
Step #9: PCI Compliance
The major credit card companies created the Payment Card Industry Data Security Standard (PCI DSS) to make sure merchants adopt critical security measures. Merchants who fail to comply with PCI requirements can expect large fines, which can also result in losing their ability to process payments.
Magento makes it easier for merchants to become PCI compliant — Magento Commerce Cloud is PCI-certified and Magento offers integrated payment gateways like PayPal, Authorize.Net, and others that securely transmit credit card info.
| 12 Requirements for PCI-DSS | |
| Build and Maintain a Secure Network | Requirement 1: Install and maintain a firewall configuration to protect cardholder data Requirement 2: Do not use vendor-supplied defaults for system passwords and other security parameters |
| Protect Cardholder Data | Requirement 3: Protect stored cardholder data Requirement 4: Encrypt transmission of cardholder data across open, public networks |
| Maintain a Vulnerability Management Program | Requirement 5: Use and regularly update anti-virus software Requirement 6: Develop and maintain secure systems and applications |
| Implement Strong Access Control Measures | Requirement 7: Restrict access to cardholder data by business need-to-know Requirement 8: Assign a unique ID to each person with computer access Requirement 9: Restrict physical access to cardholder data |
| Regularly Monitor and Test Networks | Requirement 10: Track and monitor all access to network resources and cardholder data Requirement 11: Regularly test security systems and processes |
| Maintain an Information Security Policy | Requirement 12: Maintain a policy that addresses information security |
Important Note: DO NOT USE the Saved Credit Cards Module in a Production environment!
Saved Credit Cards is not PCI-compliant and you may be exposing your customers’ credit card info.
Step #10: Install Security Extensions
When native functionality is not enough, extensions come to the rescue. Magento has a rich repository of security extensions — both paid and free. Here are a few you may try:
- BranchLabs_AdminPasswordStrength and MageHackDay_TwoFactorAuth — for secure passwords & login.
- Ikonoshirt_StrictTransportSecurity and Nexcessnet_Alarmbell — for configuration & monitoring
- MageSpecialist SecuritySuite — for Magento malware detection, reCaptcha, Admin IP restriction and two factor authentication.
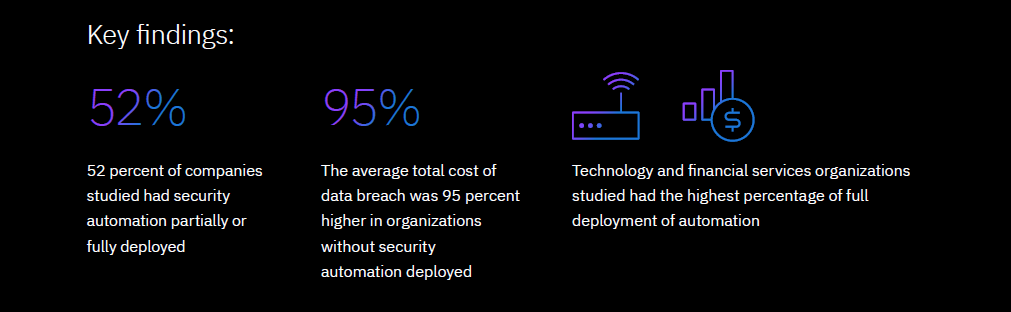
Step #11: Security Automation Solutions
Security automation is the process of automatically handling security-related tasks like antivirus scanning, intrusion detection, creating backups, renewing SSL certificates, and much more.
IBM made a groundbreaking discovery: organizations without automated security solutions experienced breach costs that were 95% higher than organizations with fully-deployed automation.
Step #12: Cyber Liability Insurance
Just like any other type of insurance (car, home, etc.) cyber insurance protects businesses from damages caused by cyberattacks. In particular, cyber liability covers
- Data breaches following employee theft and/or data leaks.
- Cyber business interruption, like a third-party hack or failed software patch.
- Data breaches following hacking.
- Errors and omissions leading to security intrusion.
Step #13: Create an Incident Response Team & Plan
If you don’t have an incident response plan (or you don’t know what this is), let’s create one.
To make it easier, we took Talesh Seeparsan’s Magento-centric Incident Response Plan Template and made a Google spreadsheet that you can copy for your own use.

Prerequisites for using the template:
- Create an Incident Response Team (IRT) to deal with security incidents for each aspect of the e-commerce solution defined in this table.
- Routinely monitor and analyze network traffic and system performance.
- Routinely check all logs and logging mechanisms, including operating system event logs, application-specific logs, and intrusion detection system logs.
- Verify your backup and restore procedures. You should be aware of where backups are maintained, who can access them, and your procedures for data restoration and system recovery. Make sure that you regularly verify backups and media by selectively restoring data.
IBM found that companies with an IRT and extensive testing of their response plans saved over $1.2 million. More specifically, the study showed that the combined effect of the IRT and testing the incident response plan, through drills and simulations, helped teams respond faster and produce greater cost savings than any single security process.
Step #14: Keep Magento Patched and Up-to-Date
There are no excuses for not having a patched and fully-updated Magento store.
To install a Magento security patch, you should
- Back up the file system, media, and database to prevent data loss in case something goes wrong.
- Download a patch (aka hotfix) from Magento security center. Mind that you’ll need to know your Magento version to download a correct patch.
- Apply a patch via Magento Quality Patch (MQP) package, command line, or Composer.
Scan your site, identify any patches you need to install, and please, do not let hackers get easy access through a vulnerability. Sign up for the Magento Security Alert Registry and make a point to visit the Magento Security Center from time to time for the latest news and information.
To save yourself some trouble, you can also hire a Magento developer. They will install a Magento security patch in no time — be it a hotfix or a custom patch.
What to Do If Your Website Has Been Hacked
Don’t panic. If there was a data breach or information exposure there’s no way of getting that information back. Your priority should be identifying what was exposed, gathering evidence, and making sure data isn’t leaking.
Follow your Incident Response Plan:
- Make an initial assessment
- Communicate the incident
- Contain the damage and minimize the risks
- Identify the severity of the compromise
- Preserve evidence
- Communicate any external notifications
- Compile and organize incident evidence
Elogic Experience with Cyberattacks
To learn what Elogic developers encounter in their work, we asked around and learned of two wild stories of malicious intent.
The Bitcoin Mining Fiasco
One of our most experienced full-stack developers at Elogic, Andriy Biloshytskiy, had an interesting experience a few years ago. Something very strange happened to one of the projects he was working on at the time.
There were no recent updates on the site, nothing had changed, except the site wasn’t working,” Andriy says. “So, I did a cursory investigation and found something both odd and amusing — there was a piece of JavaScript code with no closing tags, which caused the crash. After a Google search, I found the malicious script was intended to siphon the computing power of people visiting the store — to mine Bitcoin.
– Andriy Biloshytskiy, Full-stack developer at Elogic Commerce
The perpetrator (possibly a store admin) was never caught. The store didn’t have admin logs so there was no way to know for sure who was responsible.
The Unexpected Virus
When developers work on projects, they often clone the store on their work PC or server to test and write new code. This story happened after one of our developers cloned a store but instead of getting right to work, he saw a pop-up.
The pop-up was a warning from his antivirus software, and the source of the infection was the freshly installed Magento instance. After locating the infected file, a core PHP file, the developer deleted the malicious code and went about his job.
The moral of the story is: whether the attack is targeted, a human error, or a system glitch/vulnerability, you can help prevent breaches by implementing and following security standards.
Let Elogic audit and optimize your Magento store for you!
Request Magento code audit nowIs Magento Commerce More Secure Than Magento Open Source?
While choosing between Magento 2 Commerce vs Open Source, you might have wondered which one is more secure. While it’s true that both Magento editions deliver outstanding feature sets (depending on a merchant’s business needs, of course), we can vouch for the security of Magento Commerce (aka Adobe Commerce).
Here are five major security advantages to using Magento Commerce and Commerce Cloud.
PCI compliance
PCI compliance isn’t a feature listed in Magento Open Source, but it is in Magento Commerce. Better yet, Magento Commerce Cloud is PCI certified as a Level 1 Solution Provider, so merchants can use Magento’s PCI Attestation of Compliance to aid their own PCI certification process.
Shared security responsibilities
Magento Commerce Cloud has a shared responsibility security model where you, Magento, and Amazon Web Services (best-of-breed cloud services) share the responsibilities for operational security. You’re responsible for testing custom code and any custom applications. Magento ensures the platform itself is secure, and Amazon takes care of physical security for servers and compliance.
Action logs
Magento Commerce gives you the ability to keep a record of every change (action) made by an admin who works in your store. The logged information includes the name of the user, the action, and whether the action was successful, and it also logs the IP address and date.
Web Application Firewall (WAF)
Just like a firewall on a PC, a WAF prevents malicious traffic from entering a network by using a set of security rules. Any traffic that triggers the rules is blocked before it unleashes itself on your site or network. Magento Commerce Cloud uses Fastly CDN for WAF services.
Content Delivery Network (CDN) & DDoS Protection
Magento Commerce Cloud also uses Fastly CDN for additional security features like DDoS protection, which includes Layer 3, 4, and 7 DDoS mitigation
Takeaways — Magento Security Tips and Best Practices
Site security and more broadly, cybersecurity, should be one of your main priorities. You’re not just running a blog or personal page, you’re responsible for protecting confidential information, including names, addresses, phone numbers, and credit card info.
Remember:
- Even a fully-patched and updated site can be hacked. For example, a weak admin password can be brute-forced and hackers can stroll right in and collect everything they want. So perform Magento security checks regularly.
- You cannot account for new vulnerabilities or zero-day exploits (a cyber attack that occurs on the same day a weakness is discovered). However, a strong incident response plan can help you stay one step ahead.
- “An ounce of prevention is worth a pound of cure.” Ben Franklin was right. If you’ve configured your store with security in mind, adhered to the cybersecurity workflow we’ve outlined, and bulletproofed your store, you can save yourself tons of time and heartache.
- Do not compromise on security, or your lack of security will compromise you.
Magento Security FAQ
Is Magento Secure?
After Magento 1 fiasco, Adobe has upgraded Magento 2 to new security levels. Magento ecommerce architecture is designed to provide a highly secure environment thanks to Web Application Firewall (WAF), Fastly CDN for extra DDoS protection, and hashing to encrypt data. Security patches are released every quarter, and Magento Security Scanner is available. Merchants can additionally use SSL certificates, CAPTCHA, two-factor authentication, and other Magento security best practices to protect their customers.
So it’s safe to say that Magento is one of the most secure platforms among the ones offered in the ecommerce market.
How to Secure Magento Site?
Some best practices to secure Magento include the following:
- Provide regular audits of Magento security — be it with an automatic Magento malware scanning tool or with a help of a Magento professional.
- Use encrypted connections (SSL/HTTPS).
- Activate two-factor authentication.
- Back up your website regularly.
- Choose reliable hosting providers
- Make use of the native Magento security features and install security extensions whenever needed.
- Draw up your action plan for a cyber emergency.
See a complete Magento security checklist above.
Is Magento PCI Compliant?
Magento PCI compliance depends on its edition:
Magento Open Source is not PCI compliant, so you will have to adopt either a third-party payment method that redirects you to another site to make the transaction (like PayPal, Authorize.net) or a SaaS PCI compliant payment method (CRE Secure).
Magento Commerce and Commerce Cloud are PCI certified as a Level 1 Solution Provider.